Protecting Your Business Endpoint with Microsoft Defender
The rapid advancement nowadays in wireless communications and the computing abilities of smart devices have brought about a new era of application development.
With an increasing number of devices being equipped with technology to provide identification, computation, and communication capabilities during business operation and processes, we need to consider a system-wide security and privacy issues.
The solution to this is to have a secure endpoint that ensures data security for any interactions among endpoint devices and the back end.
What is an Endpoint?
Endpoints include the mobile devices, desktop computers, virtual machines, embedded devices, servers, and shared devices that your organization uses.
- Integrate Endpoint Management
Protecting your business endpoint can be difficult especially if employees bring their third-party devices into work and connecting them to corporate networks without alerting the right people.
It is also difficult to keep track on how many devices are connected, whether they are secure, or the types of data they are accessing.
Not to mention some of these devices, that are brought into the workplace are relatively inexpensive and they can lack legitimate security features.
Thus, when these devices enter the workplace, they can bring with them a host of security vulnerabilities that can be capitalized upon with relative ease and spread throughout the company network.
However, through the Microsoft Defender, you will be able to manage, protect and monitor all your organization’s endpoint in a single, integrated platform.
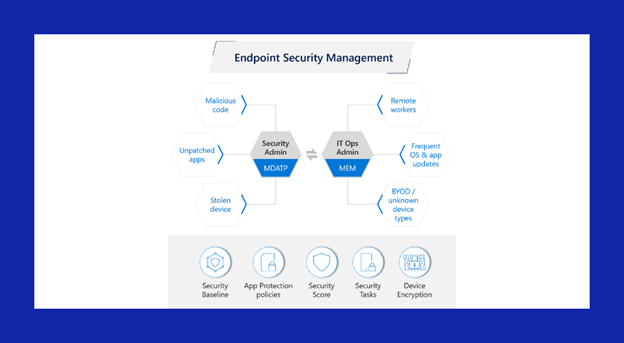
As shown in the figure above, the unified management also allows the security admin to focus and quickly act in case of any malicious code, unpatched data or stolen devices reported through all the organization’s endpoint.
At the same time, the IT operation admin manage endpoint from remote workers, or any unknown or personal devices. The Microsoft Endpoint manager also allows the admin to manage these devices’ operational system and applications updates.
- Data confidentiality, integrity, and authenticity
Besides providing an integrated platform to manage and secure the endpoint. Microsoft Defender also ensure and protect the company data confidentiality, integrity, and authenticity.
Through its feature of attack surface reduction, Microsoft Defender provides a first line of defense.
The defenses capability includes resisting attacks and exploitation of data by ensuring that configuration settings are properly set, and exploit mitigation techniques are applied on each endpoint.
This feature also capable of regulating access to malicious IP addresses, domains, and URLs.
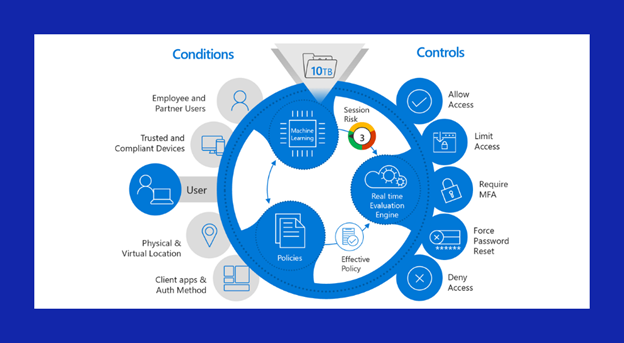
Powered by Azure Active Directory (Azure AD), Microsoft defender also ensure a secure access to the corporate resources through continuous assessment and intent-based policies with Conditional Access app controls.
The conditional access allows user to define the contextual policies at user, location, device, and app levels. As shown on the figure above, the conditional access also includes deciding which device or user to allow, limit or deny access to.
Admin or IT officer also will be able to control the requirement for a multi-factor authentication or force a password reset to the chosen endpoint.
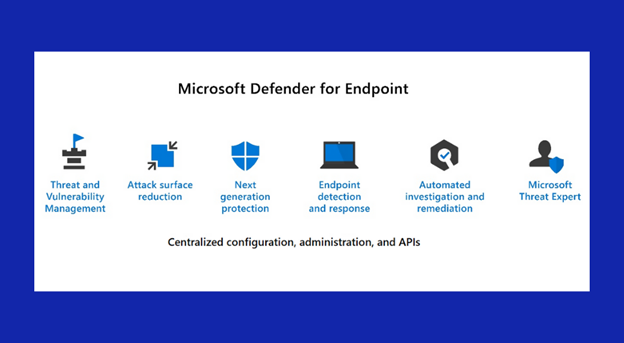
Key features of Microsoft Defender for Endpoint
Conclusion
To summarize, the increasing demand for cloud services and access increase the importance of having a strong security. But there a need of balance between strong security and allowing your users to access the data. By implementing the Microsoft Defender for Endpoint, organization could fully integrate and remove the gaps of protecting the endpoints and limiting the access of users to data.
If you are interested in knowing more about Microsoft Defender, please do not hesitate to contact us.



